Ensuring SQL data integrity and security is crucial for any database system. It ensures that data remains accurate, consistent, and secure from unauthorized access. This article delves into the core aspects of SQL data integrity and security, focusing on constraints, permissions, and best practices.
Data Integrity Constraints
- Referential Integrity: Ensures that relationships between tables remain consistent. For example, a foreign key in one table must match a primary key in another, preventing orphaned records.
- Entity Integrity: Ensures that each table has a primary key and that the key is unique and not null, maintaining uniqueness and identity.
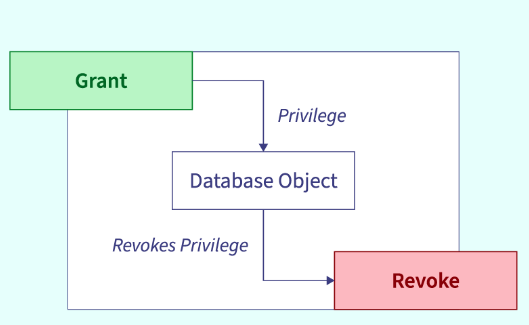
GRANT and REVOKE Statements
- GRANT: This statement is used to give users specific privileges. For example:
GRANT SELECT, INSERT ON Employees TO 'user123';This grants the user ‘user123’ the ability to select and insert records in the Employees table. - REVOKE: This statement removes previously granted privileges. For example:
REVOKE INSERT ON Employees FROM 'user123';This revokes the user’s ability to insert records in the Employees table.
Database Security Best Practices
- Use Strong Authentication: Implement multi-factor authentication to enhance security.
- Regularly Update and Patch Systems: Ensure the database software is up to date to protect against vulnerabilities.
- Encrypt Data: Use encryption to protect sensitive data at rest and in transit.
- Implement Role-Based Access Control (RBAC): Assign permissions based on roles to minimize the risk of unauthorized access.
- Monitor and Audit: Regularly monitor and audit SQL database activities to detect and respond to suspicious behavior on time.
Conclusion
Maintaining SQL data integrity and security involves a combination of constraints, permissions management, and adherence to best practices. By implementing these measures, databases can be safeguarded against inconsistencies and unauthorized access. For further insights into SQL transactions, visit our SQL Transactions Ultimate Guide.


